Kyivstar services partially restored following massive cyber attack
Services at Ukrainian telco Kyivstar have been partially restored after a widespread cyber attack took down its networks.
December 13, 2023

An update from parent company Veon said technical teams have got part of its fixed-line network back up and running, but there's no word yet on whether mobile comms and Internet services have been restored.
"Currently, the Kyivstar technical teams are working on restoring other services, with the intention of and the best effort towards achieving recovery starting 13 December 2023. The restoration of services may be gradual, and Kyivstar will inform the public and its customers as the restoration progresses," said a statement from Kyivstar.
The operator described Tuesday's cyber attack as one of the largest in the history of the global telecoms market, one that left its 24.1 million mobile customers and 1.1 million fixed-line customers unable to use its services.
One of those services is the air raid alert system.
According to the Kyiv Independent, the system was not functioning in three areas – Kyiv Oblast, Sumy, and Dnipro. It also went offline in another 75 areas, but alerts there are being sent by an alternative back-up system.
Kyivstar president Oleksandr Komarov said in a Forbes article (in Ukrainian) that the cyber attack was particularly vicious and designed to cause maximum destruction of its IT infrastructure. He said Kyivstar is working with Ericsson to restore its infrastructure, and that Microsoft is helping it to identify the root cause of the outage. Kyivstar's cyber security provider Cisco is working on strengthening Kyivstar's defenc
es.
Veon didn't point fingers at possible perpetrators, but it's a pretty safe bet where the attack originated from.
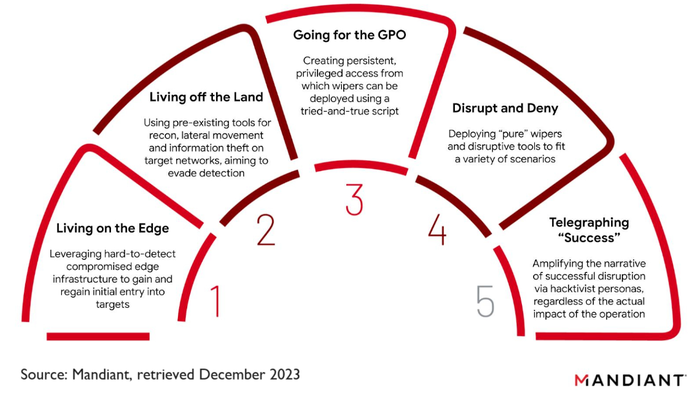
Google-owned threat intelligence specialist Mandiant in July summarised the Russian Military Intelligence (GRU)'s cyber attack strategy with a five-step playbook (see image).
Given the GRU's extensive use of wipers to destroy data on compromised machines and Komarov's reference to 'maximum destruction' of Kyivstar's IT infrastructure, the attack appears to bear the hallmarks of a Russian endeavour.
According to Forbes, the Security Service of Ukraine has opened a criminal investigation into the outage and that Russian special services are suspected of being behind it.
An unnamed source cited by Reuters insisted that a state actor is responsible, adding that intercepted data had revealed that a lot of "Russian controlled traffic" was being directed at Kyivstar's networks.
Reuters also reported that Russian hacktivist group Killnet claimed responsibility for the attack via its Telegram channel, but it didn't provide evidence to back up its claim. Nonetheless, this tallies with step five of Mandiant's playbook, which refers to amplifying the narrative of successful attacks via hacktivist groups.
Meanwhile, some outlets have reported that Ukraine has also been busy carrying out cyber attacks.
In a separate Kyiv Independent report, Ukraine's military intelligence (HUR) claimed to have hacked into Russia's tax system, extracted sensitive information, and then destroyed the database including backup copies.
It reckons it will take at least a month for the system to come back online.
With progress on the ground hitting a stalemate, it seems both sides are looking to score victories on the virtual battlefield instead.
About the Author(s)
You May Also Like











_1.jpg?width=700&auto=webp&quality=80&disable=upscale)


.png?width=800&auto=webp&quality=80&disable=upscale)